While public safety measures have started to relax, the surge of malware accompanying the pandemic is still making headlines. As a recent study points out, hackers have created no less than 130, 000 new e-mail domains related to Covid-19 to carry out what analysts now call ”fearware” attacks.
A lot of these domains and attacks are tied to the same source: the dark web. From selling vaccines and fake drugs to simply spreading panic, the dark web has been the host of many pandemic-related threats. And these attacks were just the latest addition to the dark web’s regular activity including, but not restricted to botnets, cryptojacking and selling ransomware.
However, to see how threats from the far reaches of the Internet can affect your company or clients, we must delve deeper into the concept of “dark web’’.
In the first part of our article, we try to understand the dark web’s structure and acknowledge its growing importance to cybersecurity teams.
What is the Dark Web?
Simple users or security specialists, most of us spend our time online the same way: tied to a few popular websites and chat clients or perusing pages through a search engine. This activity, mediated by traditional browsers and apps, accounts for an almost endless amount of content.
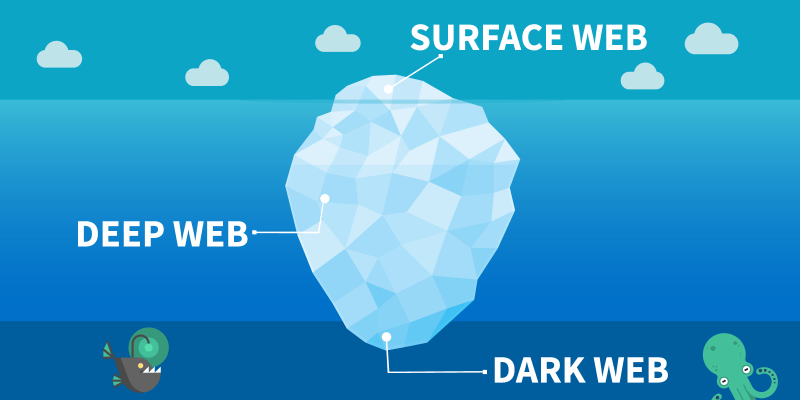
But, as copious as this content might seem, it’s only a small percentage of what the Internet has to offer – as little as 4%, according to CSO Online. The rest of it? An enormous collection of unindexed websites, private pages, and secluded networks that regular search engines cannot detect, bearing the generic moniker of ‘’deep web’’.
The deep web covers just about anything that’s hidden from the public eye, including exclusive and paid content, private repositories, academic journals, medical records, confidential company data and much more. In a broad sense, even the contents of an e-mail server are part of the deep web.
However, there is a certain part of the deep web that’s noticeably different. How? Well, if the deep web in general is content that can’t be found through conventional means, the dark web is that part of it that does not want to be found.
The dark web exists through private networks that use the Internet as support, but require specific software to be accessed, as well as additional configurations or authorization. While the dark web is only a small part of the deep web, it allegedly still accounts for around 5% of the entire Internet… and for a lot of its malicious activity.
Since the dark web can’t be accessed directly, users need to use special software such as the Tor browser, I2P, or Freenet. Tor, also known as The Onion Router, is perhaps the best-known means of accessing the dark web, as it is used both as a gateway and a security measure (limiting website interactions with the user’s system). While the protocol itself was initially developed by a Navy division before becoming open source, the project is currently administered by an NGO.
I2P (The Invisible Internet Project) specializes in allowing the anonymous creation and hosting of websites through secure protocols, directly contributing to the development of the dark web.
At this point, it’s worth stating that many dark web sites are not in any way malicious and might just be private for security reasons (journalism websites for countries where censorship is rampant, private chat rooms for people affected by trauma, etc.). It’s also worth noting that platforms such as Tor are not malicious in themselves, with their technology being also used by many legitimate companies. However, the dark web offers two very powerful abilities to its users, both of them ripe for abuse.
These abilities are complete anonymity and untraceability. Unfortunately, their dangers only became visible after Silk Road, probably the world’s largest illegal online market at the time, was closed. A similar ripple was also produced by the closing of the gigantic Alphabay, an even more comprehensive follow-up to Silk Road.
The Dangers of Anonymity
The truth is, dark web sites have been known to sell just about anything from drugs and contraband, guns, subscription credentials, password lists, credit cards to malware of all types, as well as multiple other illegal wares. All without any real control, from website owners or authorities, and all under the guard of encryption. Back in 2015, a study classified the contents of more than 2,700 dark web sites and found that no less than 57% hosted illicit materials!
Obviously, this prompted authorities to take action. Some law enforcement agencies have started monitoring Tor downloads to correlate them with suspicious activity, while others, such as the FBI, established their own fake illegal websites on the dark web to catch wrong-doers.
Even with such measures in place, the dark web’s growth is far from coming to a halt. Its traffic actually increased around the Covid-19 pandemic, and the technology’s 20th anniversary. It is estimated that in 2019 30% of Americans were visiting the dark web regularly, although mostly not for a malicious purpose. Furthermore, as large social networks increase their content filtering and as web monitoring becomes more prevalent on the „surface web”, the dark web is slowly becoming an ideological escape for certain vocal groups.
While these numbers can put things into perspective, many security experts, from both enterprise organizations and MSSPs, might ask: ”Alright, but what does that have to do with my company? Why do I have to monitor the dark web?”
To learn more about how Granite Discovery can help you, contact us today. Click here.
by Andrei Pisau
To view original post, click here.
Published: May 29, 2020