Harnessing Logical Evidence in Digital Forensics Investigations
Logical evidence is now essential for solving cybercrimes and revealing hidden realities in the quickly changing digital world of today. Logical proof is essential when looking into corporate data breaches or following digital footprints in court proceedings. As our reliance on technology grows, it becomes harder for businesses and the police to handle huge amounts of digital data. Metadata, log files, and user behavior are all examples of logical proof that can be used to recreate events and find those responsible. If you use reasoning facts correctly, it leaves no room for doubt, unlike actual proof. This article explores the definition, importance, and techniques surrounding logical evidence in digital forensics. By understanding its applications, challenges, and tools, professionals can harness it to solve cases with precision and confidence.
- Understanding Logical Evidence
- The Role of Logical Evidence in Digital Forensic Investigations
- Techniques for Analyzing Logical Evidence
- Case Studies
- Challenges and Future Trends
- Conclusion
Understanding Logical Evidence
-
Types of Logical Evidence
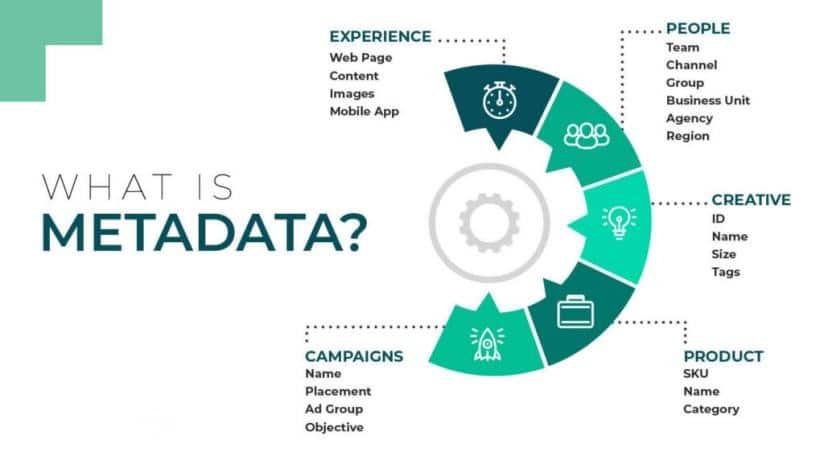
Logical evidence refers to digital data that provides insight into activities, events, and system behavior. It plays a vital role in uncovering key information in digital investigations. The primary types of logical evidence include:
- Metadata: Hidden information within files, such as creation date, modification time, and user details.
- Log Files: Detailed records of events occurring within a system, network, or application.
- System Configurations: Settings and configurations that document system-level changes or activities.
- User Activity Data: Information about user actions, including logins, file access, and browsing history.
By leveraging these data points, investigators can establish timelines and pinpoint anomalies within digital systems.
-
Comparison Between Logical and Physical Evidence in Digital Forensics
Hard disks and USB devices are examples of physical evidence, while logical evidence concentrates on intangible data like log files or metadata. Though logical evidence may provide comprehensive recordings of user behaviors and is often simpler to assess remotely, both are crucial.
Physical proof, on the other hand, usually needs to be looked at in person. Using both types of proof together makes probes stronger and makes sure that the results are correct and full.
By understanding the significance of logical evidence examples and its distinction from physical evidence, digital forensic professionals can make more informed decisions during their investigations.
The Role of Logical Evidence in Digital Forensic Investigations
-
Establishing Timelines and User Activities
Logical evidence is essential to digital forensic investigations because it helps create comprehensive timelines and pinpoint user activity. Log files, system settings, and user activity records are examples of data that assist investigators in determining who did what and when. For instance, the precise time of creation, modifications, or access may be shown in the metadata of documents or files. Experts are able to precisely recreate events by examining these bits of data. Solving situations involving fraud, data breaches, or illegal access requires this stage.
-
Supporting Court Cases with Accurate Data
Logical evidence examples are often presented in courts to provide accurate and admissible information. Whether it’s digital evidence like emails, log files, or browsing history, logical data is critical for proving actions or intentions. Unlike physical evidence, logical evidence can document precise user activities and timelines, leaving little room for doubt. Courts value such data because it offers a clear, factual representation of events, strengthening legal arguments and supporting justice.

-
Addressing Issues of Tampering, Integrity, and Chain of Custody
Despite its importance, logical evidence faces challenges related to tampering and maintaining integrity. Digital data can be altered, intentionally or unintentionally, making it essential to ensure a clear chain of custody. This means evidence must be collected, stored, and transferred securely, without risk of manipulation. Tools like digital forensics software help maintain evidence integrity by using hashing techniques to verify data authenticity.
Investigators can make sure that the data they collect is accurate and can be used in court by knowing how to gather, store, and show reasonable proof. The key to successful digital forensic investigations is getting past these problems.
Techniques for Analyzing Logical Evidence
-
Common Tools and Methodologies for Analyzing Logical Evidence
The process of analyzing logical evidence requires specialized tools and methodologies to ensure accuracy and efficiency. These tools help digital forensics professionals extract, examine, and interpret data effectively. Here are three key tools, including one from SalvationDATA:
- SPF Pro (SalvationDATA): A leading digital forensics tool, SPF Pro specializes in analyzing system logs, recovering deleted data, and ensuring evidence integrity. It’s trusted for its accuracy and user-friendly interface, making it a go-to choice for professionals.
- FTK (Forensic Toolkit): Widely used in digital forensics, FTK allows for in-depth analysis of files, metadata, and log activities. It helps extract logical evidence examples like user activity data and system configurations.
- X-Ways Forensics: Known for its efficiency, this tool aids in recovering digital evidence and identifying user behavior through log files and metadata analysis.
These tools provide comprehensive solutions for collecting and interpreting logical data, which is essential for building a strong forensic investigation.
-
Steps to Ensure the Reliability and Accuracy of Evidence Handling
To maintain the integrity of logical evidence, strict protocols must be followed:
- Proper Collection: Evidence must be collected from the source using forensically sound tools to prevent any alterations.
- Chain of Custody: Maintaining a clear record of who handled the evidence ensures accountability and prevents tampering.
- Hashing for Integrity: Hash values (e.g., MD5, SHA-256) are generated to verify the authenticity of logical evidence during transfer and analysis.
- Secure Storage: Evidence should be stored securely in encrypted containers to protect it from unauthorized access.
- Documentation: Every step, from collection to analysis, must be thoroughly documented to ensure transparency and reliability.
By utilizing advanced forensics tools and adhering to strict handling protocols, professionals can extract and present logical evidence with confidence and accuracy. These techniques are critical for solving complex cases and ensuring evidence remains admissible in court.
The original article was written on 02/15/2025 and can be found here.
Contact Granite Discovery to learn more about our services and how we can help you.



